Dark Web: How The Unseen Internet Is Accessed
In 2015, the founder of a website called the Silk Road was sentenced to life in prison. The billion-dollar black market site was once the premiere online bazaar for drugs and other contraband, but it remained hidden from casual internet users for years because of something called the dark web.
Here’s how that dark side of the internet actually works.
Anatomy of the internet
If you think of the web like an iceberg, you have the surface web up top. It’s the internet you see and use every day and consists of all the websites indexed by traditional search engines like Google. It’s where you shop on Amazon and listen to music on Spotify.
What’s submerged is the deep web — an anonymous online space only accessible with specific software. Then there’s the dark web, which is the part of the deep web that hides your identity and location.
It’s basically just “a series of encrypted networks that serve to anonymize peoples’ use on the internet,” said Matthew Swensen, a Special Agent for the Department of Homeland Security with an expertise in cyber crimes.
It’s relatively easy for anyone to access this encrypted network. All it takes is downloading darknet software. Swensen said the most common dark web networks are Tor, I2P, and Freenet, but “Tor is, by far and away, the most popular.”
Tor
Tor stands for “the onion routing project.” It was developed by the U.S. Navy for the government in the mid-1990s. But it was open-sourced in 2004, and that’s when it went public. Tor is now the dark web browser that the vast majority of people use to anonymously surf the internet.
To understand how Tor actually works you need to know what happens when you typically search the web. Think of your IP address as an online identity. Any device you use to connect to the internet has one. Each time you visit a website, you can be traced back to your exact location thanks to that IP address.
The Tor browser looks like any other, except that there’s a whole lot happening that you don’t see. Instead of your connection request bouncing from its origin right to its destination, Tor sends your request on a much more roundabout route.
Let’s say you’re in New York and you want to search a site hosted in New Jersey. Instead of connecting you directly, the Tor browser takes you on at least three random detours called relays. Your request could go from New York to South Africa, from South Africa to Hong Kong and from Hong Kong to New Jersey.
Tor is comprised of people from all over the planet who are donating their computers to the network. It has more than 7,000 relays to choose from. Bouncing your request around to random computers all over the world makes it much harder for people to find you.
Software firm Hyperion Gray put together a map showing all 6,608 dark web sites crawled during January 2018. Each screenshot is a site, and the content ranges from the nefarious to the noble.
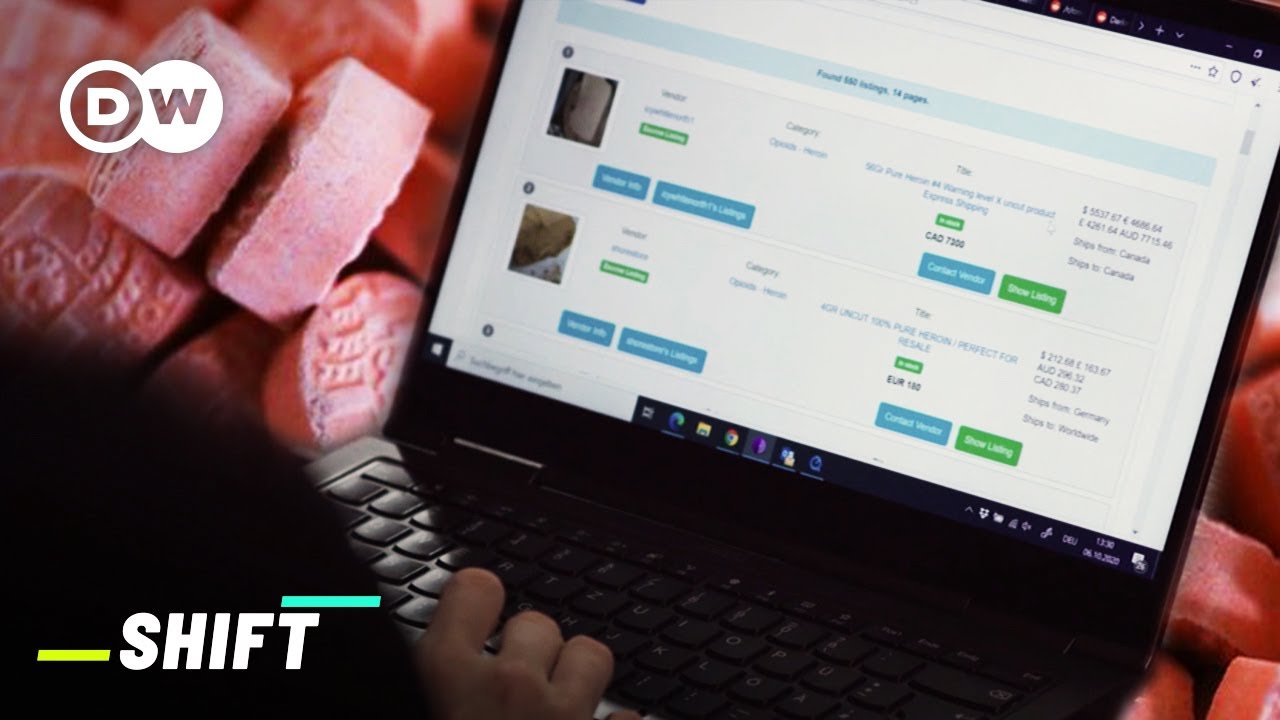
For some users — like journalists or whistleblowers — the dark web is about identity protection. It’s where individuals can share anonymous tips with the press on secure drop sites. But more often than not, it’s tied to the world of cybercrime. Special agents like Swensen are looking for the kinds of users who want this full cloak of anonymity in order to mask their illegal activity.
Putting a stop to this kind of crime has been described as a “never-ending game of whack-a-mole” for law enforcement. But even with the odds seemingly stacked against it, the anonymity of the dark web can sometimes play to the law’s advantage. No ID and no location means you never really know who’s communicating with you.
» Subscribe to CNBC Make It.: http://cnb.cx/2kxl2rf
About CNBC Make It.: CNBC Make It. is a new section of CNBC dedicated to making you smarter about managing your business, career, and money.
Connect with CNBC Make It. Online
Get the latest updates: https://www.cnbc.com/make-it
Find CNBC Make It. on Facebook: https://cnb.cx/LikeCNBCMakeIt
Find CNBC Make It. on Twitter: https://cnb.cx/FollowCNBCMakeIt
Find CNBC Make It. on Instagram: https://bit.ly/InstagramCNBCMakeIt
#CNBC
Dark Web: How The Unseen Internet Is Accessed


![Bank Heist (Joker) | The Dark Knight [IMAX]](https://i.ytimg.com/vi/vetKTtM7YyU/maxresdefault.jpg)



















SORT BY-
Beste Kommentare
-
Neueste Kommentare